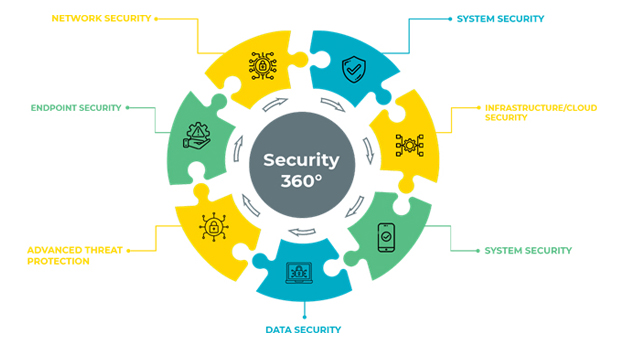
Hardware and software security must be implemented and maintained with the appropriate level of technical and administrative controls to ensure and protect organizations critical important data from intentional or unintentional unauthorized use, modification, disclosure, or destruction. Usually, computer hardware administrators think primarily about software-based solutions such as anti-malware and antivirus software solutions.

Security Solutions
Hardware security is vulnerability protection we provide which comes in the form of a physical device rather than software that is installed on the hardware of a computer system.
Physical Security
We assure the protection of personnel, hardware, software, networks and data from physical actions and events that may cause loss or damage to the systems.
Surveillance camera
Surveillance cameras used for the purpose of observing and monitoring a required area. They are connected to a recording device or IP network.
PARTNERS



Firewall

Firewall is a network security device that monitors and filters incoming and outgoing network traffic based on the desired security policies. Usually, a firewall is the essential barrier that sits between a private internal network and the public Internet.
PARTNERS



End Point Security

Endpoint security is the practice of securing endpoints or entry points of end-user devices such as desktops, laptops, and mobile devices from being exploited by malicious actors and campaigns. Endpoint security systems protect these endpoints on a network or in the cloud from cybersecurity threats.
PARTNERS
Monitoring Tools

Monitoring tools are used to continuously keep track of the status of the system in use, in order to have the earliest warning of failures, defects or problems and to improve them. We provide monitoring tools for servers, networks, databases, security, performance, website and internet usage, and applications.
PARTNERS
Servers

It is a type of computer or device on a network that manages network resources. Servers are often dedicated, meaning that they perform no other tasks besides their server tasks. On multiprocessing operating systems, however, a single computer can execute several programs at once.
We have server solutions for all kinds of needs and requirements. We can help you with file server solutions to keep your official data secure and centralized. You can also run to us with your needs of the application server as it will run CRM, ERP, and other centrally controlled applications.
PARTNERS
Virtualisation And Vdi Solution
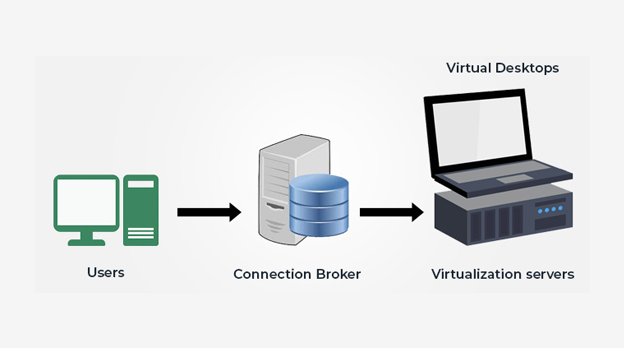
Process of running a virtual instance of a computer system in a layer abstracted from the actual hardware commonly, it refers to running multiple operating systems on a computer system simultaneously. To the applications running on top of the virtualized machine, it can appear as if they are on their own dedicated machine, where the operating system, libraries, and other programs are unique to the guest virtualized system and unconnected to the host operating system which sits below it.
Virtual desktop infrastructure (VDI) is a virtualization solution that uses virtual machines to provide and manage virtual desktops. VDI hosts desktop environments on a centralized server and deploys them to end-users on request. accessed over the network with an endpoint device such as laptop, tablet, and so on.
PARTNERS



Back up Solutions

As data has become a mission-critical asset for business, IT organizations need backup solutions that can effectively protect data from loss, corruption, compromise and theft. PCT offers data protection software, appliances and backup solutions that help dramatically simplify data backup, recovery and archiving while reducing costs and effectively protecting data from a variety of threats. Simple to deploy and easy to manage, PCT help protect data no matter where it resides to improve uptime and maximize the value of business data.
PARTNERS


Storages

Data may be stored on premises, on external drives, on remote devices, on removable media, or online (in the cloud). For large amounts of data, businesses often use storage area networks (SANs), network-attached storage (NAS) devices, software-defined storage (SDS), or cloud-based storage.
PARTNERS




Network Switches

Network switch is defined as a hardware component responsible for relaying data from a computer network to the destination endpoint through packet switching, MAC address identification, and a multiport bridge system. A network switch connects devices within a network (often a local area network, or LAN*) and forwards data packets to and from those devices.
PARTNERS






Access Points / WIFI

It is a device that creates a wireless local area network, or WLAN, usually in an office or large building. An access point connects to a wired router, switch, or hub via an Ethernet cable, and projects a WiFi signal to a designated area.
PARTNERS


Mobile Device Management
Mobile Device Management is any software that allows IT to automate, control, and secure administrative policies on laptops, smartphones, tablets, or any other device connected to an organization’s network.
PARTNERS


Data Leak Prevention

Data Loss Prevention (DLP) is the practice of detecting and preventing data breaches, exfiltration, or unwanted destruction of sensitive data. Organizations use DLP to protect and secure their data and comply with regulations.
PARTNERS



Annual Maintenance Contract

- NON COMPREHENSIVE – for IT Assets – by PCT
- COMPREHENSIVE – TIED up with SOLID GOLBAL SYSTEMS ( Only servers, switches workstations camera etc )
IT Accessories and End Point

We recommend computer peripherals as per your IT requirements, that exactly meet your requirements.
Endpoints are physical devices that connect to and exchange information with a computer network. Some examples of endpoints are mobile devices, desktop computers, virtual machines, embedded devices, and servers.
PARTNERS



Networking

IT network is the backbone of the business as it connects all its computers and related devices together, allowing staff to work more efficiently across the organization. Networking is a set of computers sharing resources located on or provided by network nodes. The computers use common communication protocols over digital interconnections to communicate with each other.
PARTNERS






